String Encryption
Overview
Dotfuscator allows you to hide user strings that are present in your assembly. A common attack technique is to locate critical code sections by looking for string references inside the binary.
For example:
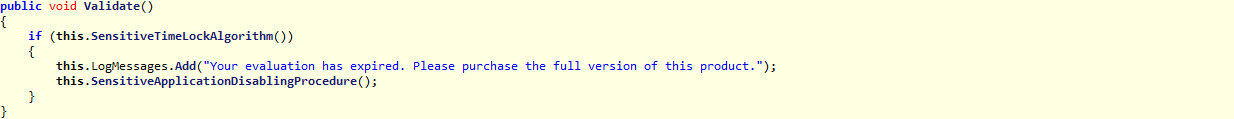
- If your application is time locked, it may display a message when the timeout expires. Attackers search for this message inside the disassembled or decompiled output, and chances are, when they find it, they will be very close to your sensitive time lock algorithm.
- Someone looking to bypass your registration and verification process can search for the string where your program asks the user for a serial number. When they find the string, they locate instructions near it and alter the logic.
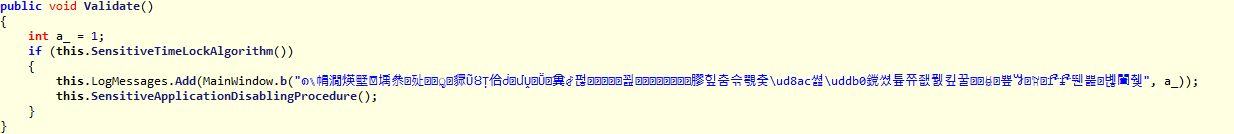
By scrambling the strings in your application, String Encryption makes both of these attacks less likely, because the attackers' string searches will come up empty.
Example
Before:
After:
Limitations
const strings are not encrypted, but all the places that use them are updated with encrypted versions of the string.
To get around this, enable Removal, and set Removal | Options | Removal Kind to Remove only literals (const definitions).
If some computationally intensive (highly repeated code) is generating strings (maybe for logging purposes), then there may be performance degradation as extra method calls must be performed to decrypt those strings.
Specifying Inclusions
Unlike Renaming and Control Flow which transform as much code as they can unless you specifically exclude items, String Encryption by default encrypts no strings whatsoever. To enable encryption of all strings in an assembly, simply go to the String Encryption | Include tab, and click the checkbox on the assembly node (which will recursively check all subitems).