Released on September 31, 2016, Dotfuscator Professional 4.25 includes, for the first time, the ability to inject real-time detection, defense, and notification of unauthorized debugger use against production applications.
Within the first two weeks of availability, 40+ development organizations kicked-off projects to implement these controls. While the pace of adoption is unprecedented, it’s the composition of this first wave of adopters that is especially significant.

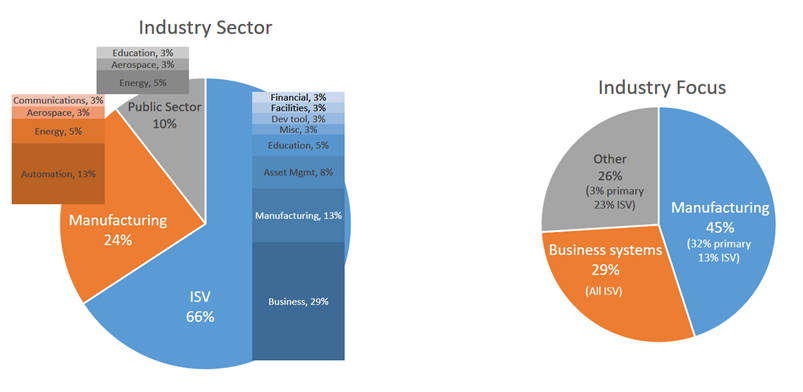
Charting early adopter industry sectors and their respective industry focus
The first chart divides early adopters by their industry sector. While it may not be surprising to see 66% identify as ISVs, the fact that equipment manufacturers make up the remaining portion of the private sector at 24% is certainly noteworthy.
The second chart divides the early adopters by their industry focus, e.g. who are their target users? Equipment manufacturing becomes even more dominant in this context as more than half of the public sector and a fifth of the ISVs are targeting equipment manufacturer users as well – bringing manufacturing application development to 45% of the early adopter community – the largest by far.
Half of the ISV community (29% overall) develop business applications and services – which, while not as striking as manufacturers, is still a greater percentage than all of the other (non-manufacturer) categories combined.
What do business systems and manufacturing applications have in common that make debugger hacking controls particularly important?
Let’s start with what sets debugger hacking controls apart from Dotfuscator’s current set of application security controls such as obfuscation or Dotfuscator’s ability to inject feature and exception monitoring.
Manufacturing and business applications are most likely to:
It doesn’t really matter if you develop manufacturing or business applications, if your applications share any of the above traits, we would recommend taking a much closer look at both the risk that this kind of exploit may pose to your organization and the extent to which the debugger-defense controls now available in both Dotfuscator Professional for .NET (AND DashO for Java and Android) can help mitigate those risks.
For more information, visit Top 5 reasons why Dotfuscator’s new anti-debugging and anti-tamper technology is changing the way developers manage risk. NOTE the opportunity to download a white paper from that page as well.