Pokefan Alert – augmented reality apps like Pokemon Go are rooted in the REAL WORLD (not a virtual one) – a real world with a host of very real dangers.
Pokemon Go players are walking into traffic, being lured into remote locations to be robbed, and last (but in no way least) they’re being duped into using counterfeit (tampered) Pokemon Go apps.
What’s the harm? The “Gucci” handbag I bought off the street doesn’t seem like much of a threat.
Given the central role of mobile devices in every aspect of our lives, counterfeit apps now pose as great a threat to public and personal safety as counterfeit medications or car parts. A mobile app with malware can take over your phone, your credentials, and your identity (way more toxic than a handbag with a fake fashion logo) – and, when considering something as wildly popular as Pokemon Go, mobile apps are also at least as lucrative a target for cut-throat criminals as well.
This is not a hypothetical – Researchers at proofpoint have already found hacked versions of Pokemon Go on Android – and there’s no reason to believe that there’s not an all-out race within the criminal hacker community to exploit the tremendous popularity of this (and any other) wildly popular app.
It’s actually not too difficult to avoid counterfeits. Do not be tempted to side load Pokemon Go directly from a download; do not be tempted to go to a secondary app marketplace (other than Google Play or the iStore) – even if you’re in a region where Pokemon Go hasn’t been officially released. It’s simply not worth it.
You cannot passively ignore the responsibility that comes with any success that may come your way – the more popular (or mission critical from a business perspective) your work becomes, the more attractive your code becomes to attackers. If Willie Sutton were alive today, he wouldn’t rob banks – he’d be a hacker “because that’s where the money is.”
Application security and risk management (being a part of the “real world”) is not much different than any other flavor of security and risk management – to be effective, security controls need to be proportionate, layered, and consistently applied.
For consumer apps like Pokemon Go (and line of business apps too) this means understanding how hackers attack and setting up material obstacles at every turn – impeding (if not deterring) exploits and (when attacks succeed as they will from time-to-time) enhancing prosecution and punishment.
I have no personal knowledge of the precautions the authors of Pokemon Go have taken as a part of their development process – but let’s hope that they have implemented a layered approach designed to halt, delay, or at least discourage a would-be hacker at every step in their journey.
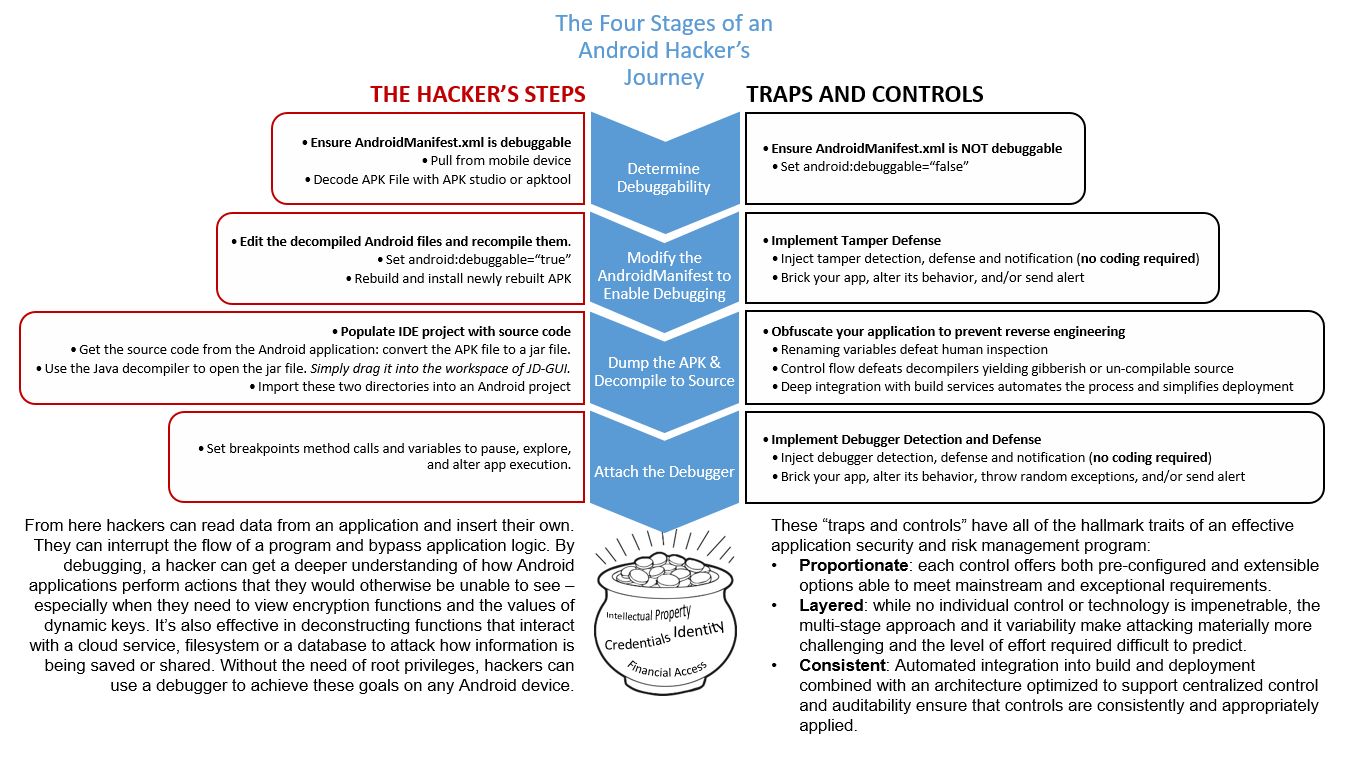
The following graphic outlines a typical Android hacker’s journey; the steps they are likely to take on one side and the traps and controls that can trip them up on the other such as Android obfuscation and anti-tamper technologies.
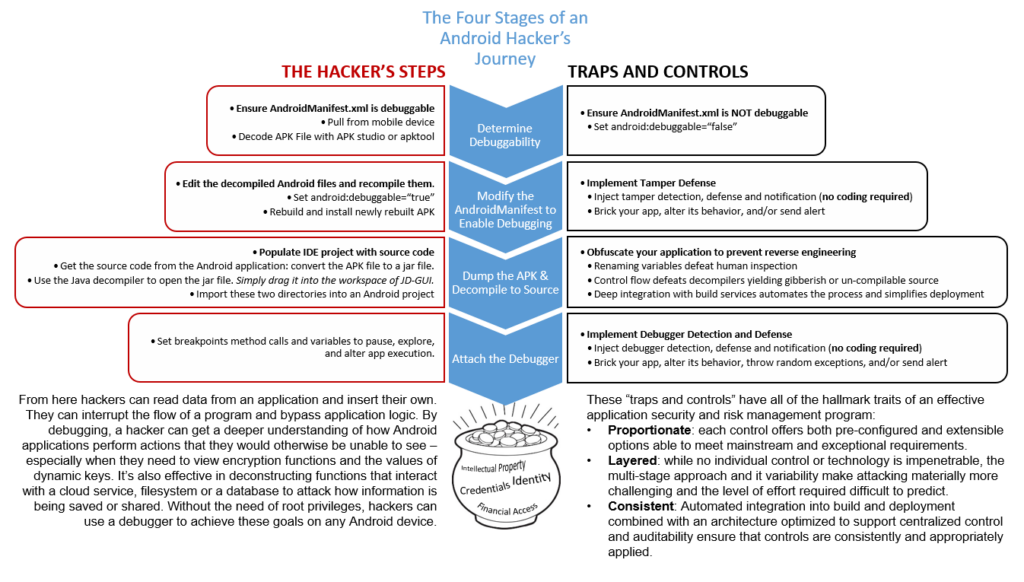
Whether for selfish reasons (you don’t want to be the guys whose app screwed everything up), or ethical obligations (you know that you owe it to your user community), or legal risk (the courts are far from settling what kind of liability comes with deploying unsafe software ripe for exploitation) – there can be no doubt; app owners must bake effective risk management and security controls (devsecops) into every facet of their application’s lifecycle; from design through deployment and deprecation.
For more information on how to best manage application risk and secure intellectual property across mobile, on-premises and cloud-based development investments, contact solutions@preemptive.com or check out more information on DashO.