A good app hardening tool goes beyond just renaming code! Your application needs a multi-layered approach to obfuscation to remain truly safe from hacking and data breaches.
Explore how DashO allows you to take a more proactive approach to Java and Android app security with multiple layers of protection.


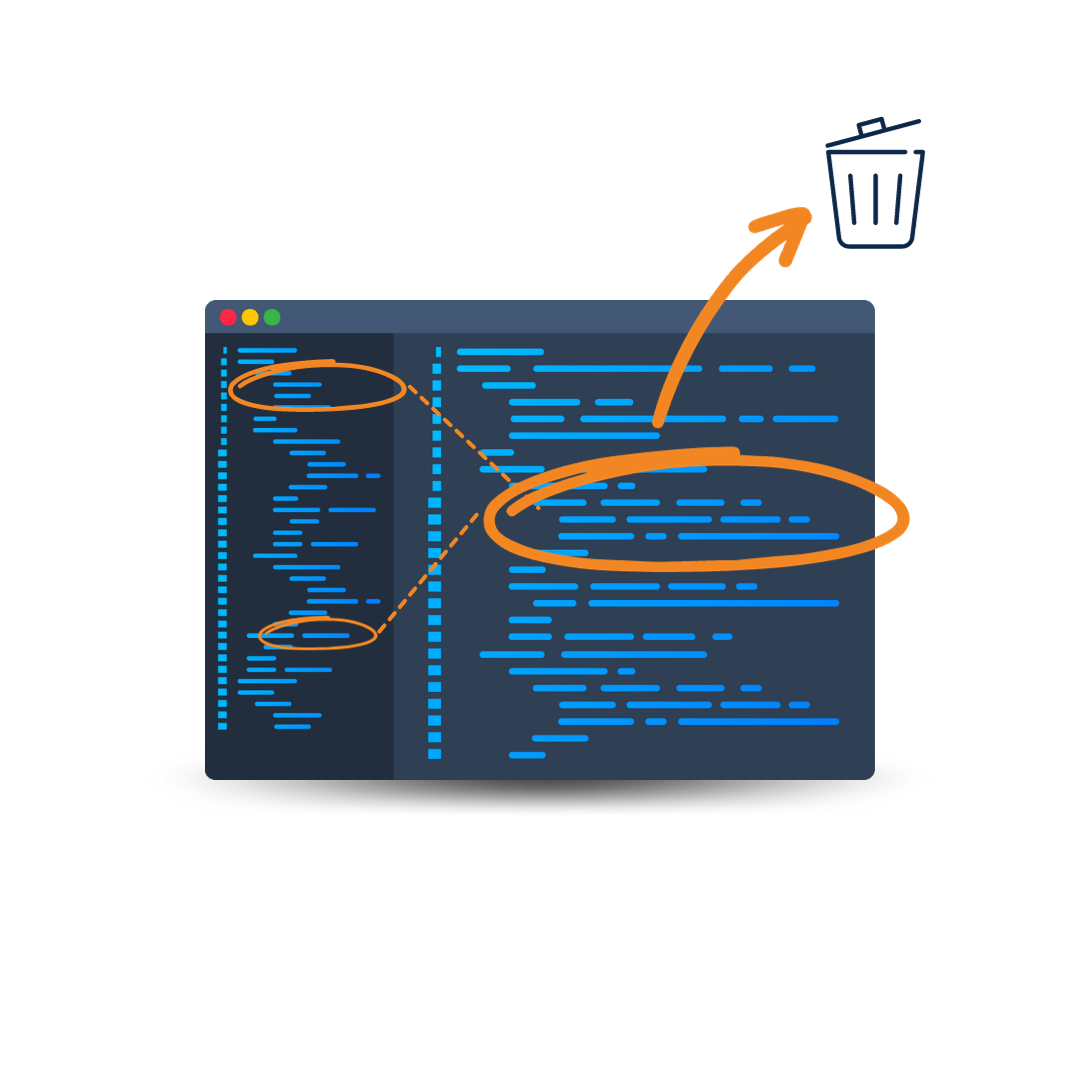


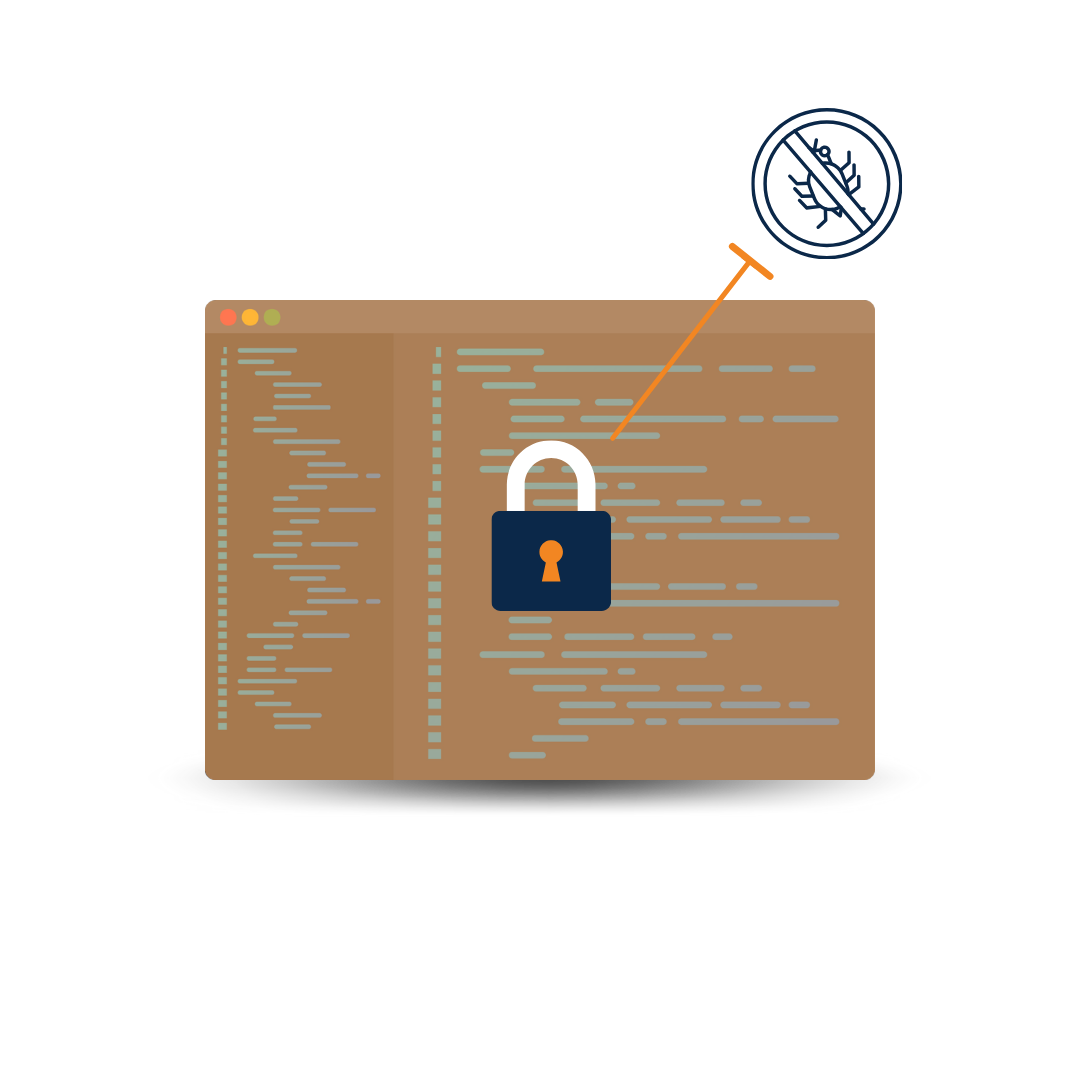


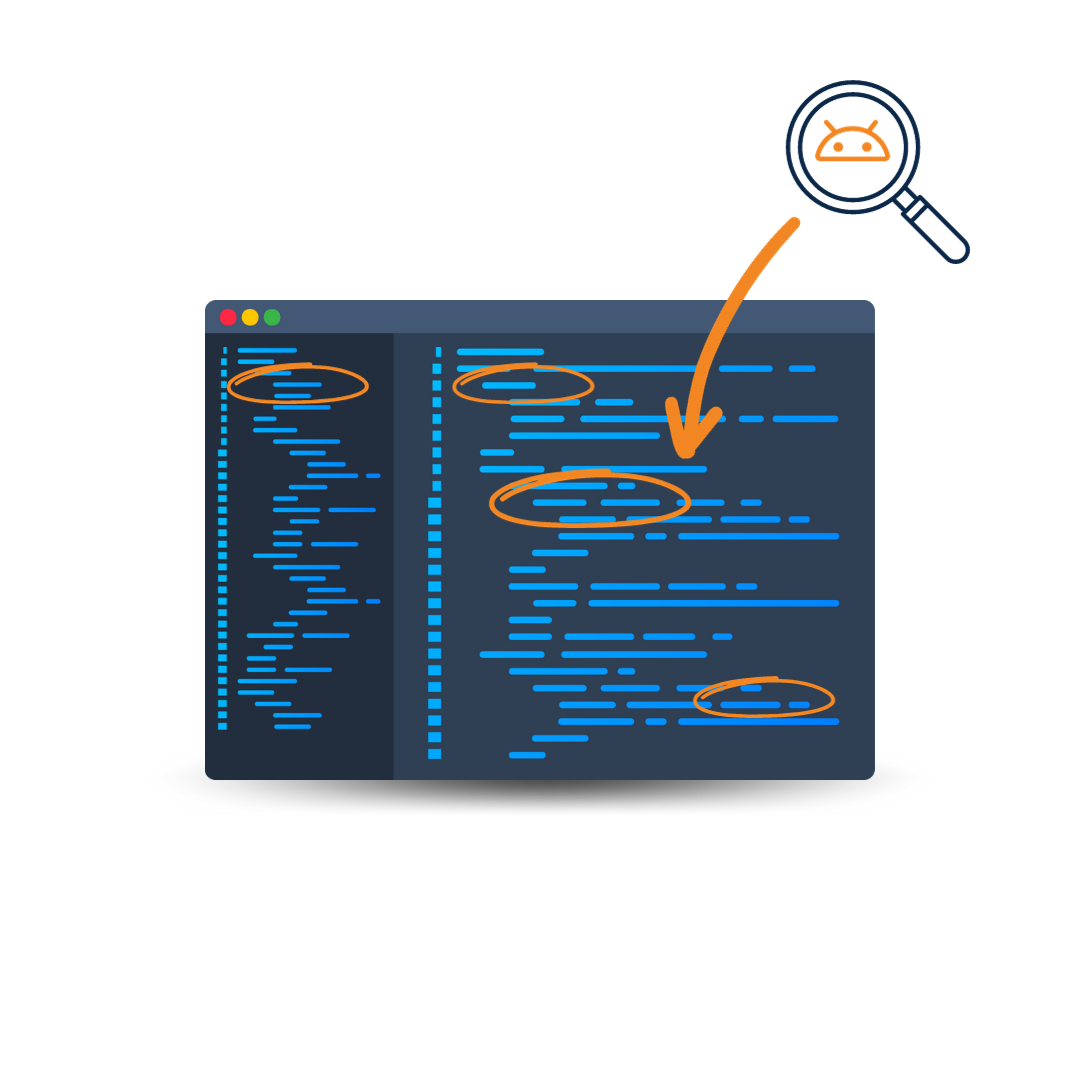

Want to try DashO for yourself? Download a free trial of DashO today or request a quote and see how you can elevate your app security today.