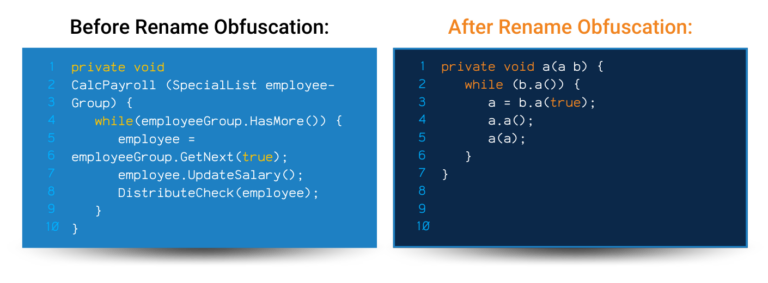
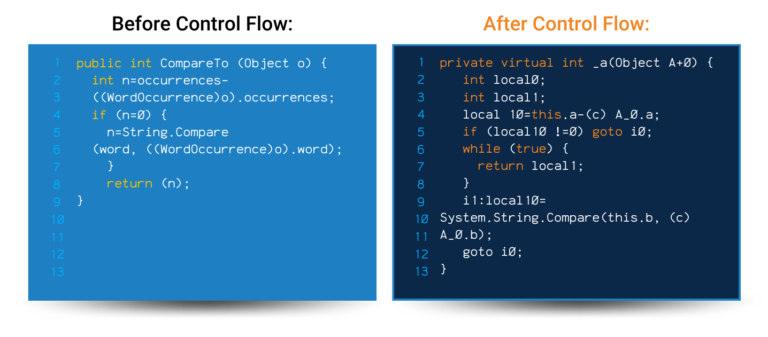
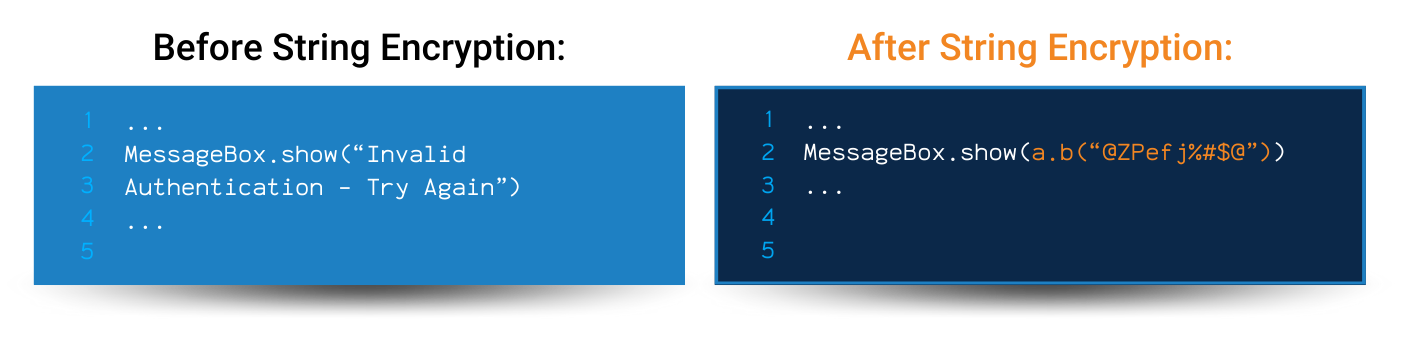
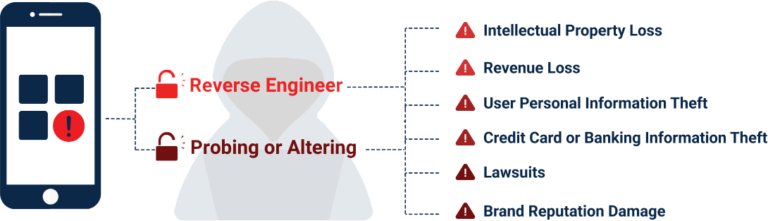
App hardening is essential for protecting your work and keeping your users safe. However, to have a truly secure application, you need to take a layered approach to security with multiple code obfuscation techniques in place.
Discover the features Dotfuscator offers and how they can help you get the protection your app needs.