
Visual Studio Tools for Office (VSTO) have enabled .NET developers to extend the functionality of Office applications like Word, Outlook, and Excel since 2003. VSTO Add-Ins are deployed directly to the end user’s machine and triggered when the Office application starts. Because of this, VSTO Add-Ins can be easily decompiled and reverse engineered like other .NET applications. As many developers can attest, this is an easy access point for hackers to gain control of your applications.
Most application hardening techniques are quite cumbersome for VSTO Add-Ins. After application hardening, the VSTO application manifest (.manifest) and deployment manifest (.vsto) must be manually created or updated using the Mage tool. Signing of assembly and manifest files must be done separately as well.
Fortunately, protecting VSTO Add-Ins is made simple with PreEmptive’s Dotfuscator. All we have to do is edit the project file (.csproj, .vbproj) to add tags that call Dotfuscator.
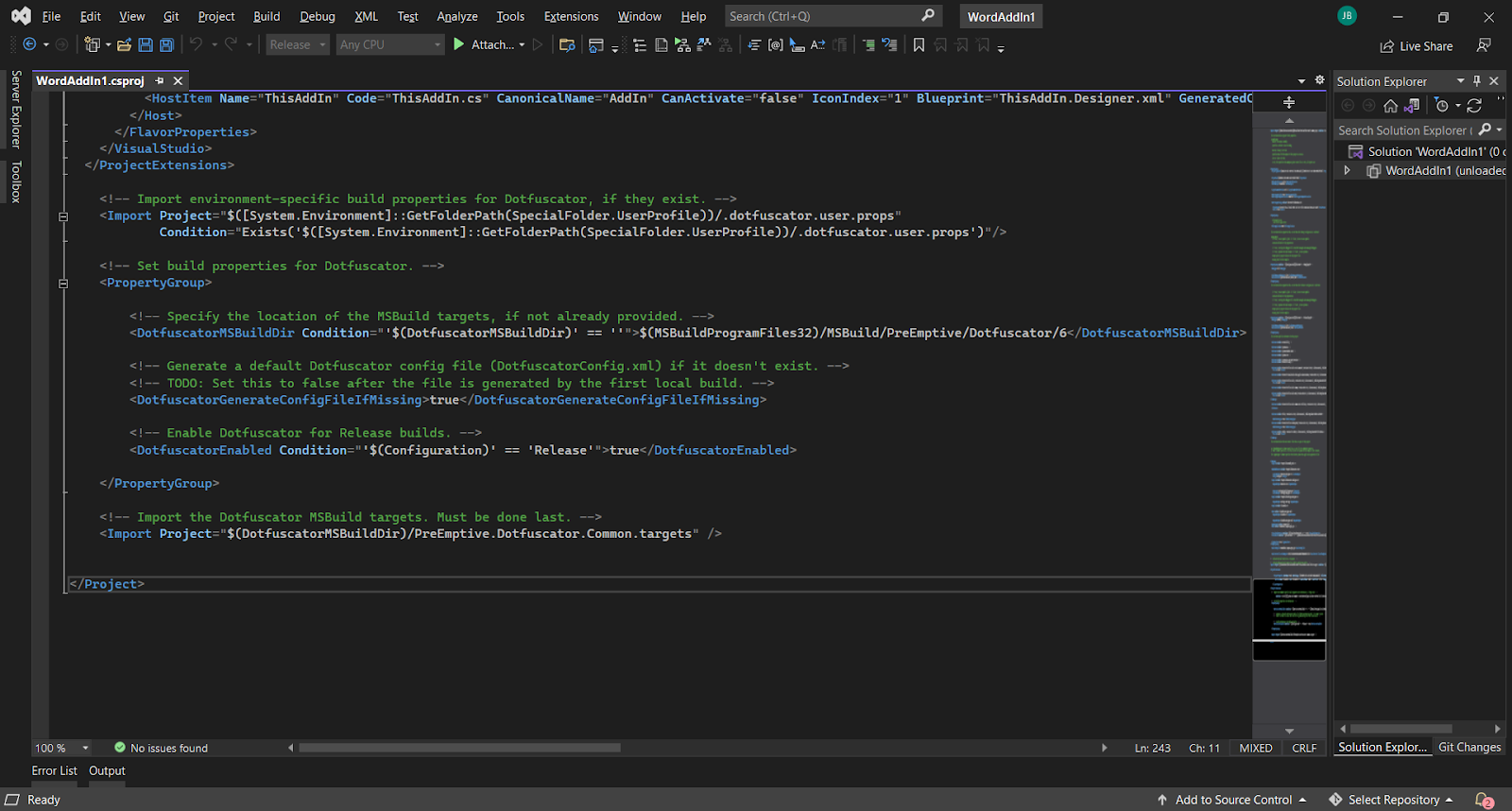
This will trigger Dotfuscator to run before packaging steps of our build, so protected binaries are automatically packaged for deployment. This works whether we’ve created an installer or are using ClickOnce. No additional steps are required and developers can implement it relatively easily.
A simple VSTO Add-In with Dotfuscator integration can be downloaded here. A release build automatically generates obfuscated binaries, and double clicking the .vsto manifest installs the Word Add-In.
Although VSTO Add-Ins are being phased out in favor of the new Office Add-in, there are still several VSTO applications in production which could benefit from Dotfuscator’s simple integration. If you have questions on this or other topics you would like us to discuss in the Support Corner, please feel free to contact our Support Department.