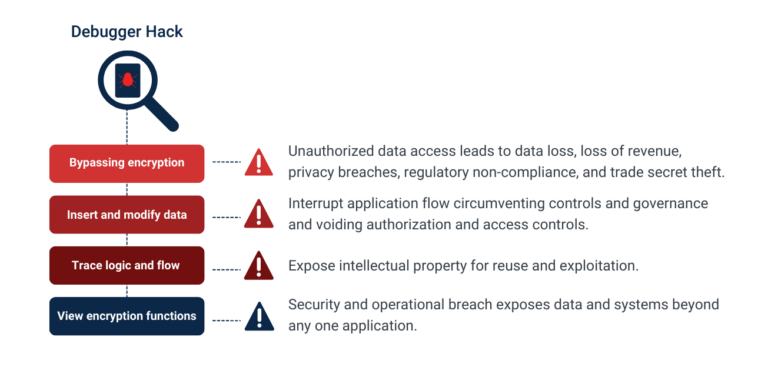
Whether you’re building applications for sale, as a key part of a larger financial or manufacturing business, or as part of a line of business apps for internal use, there is likely to be IP (trade secrets) within your software. And possession of functioning source code provides transparent access to any IP that is coded within the application. So, a hacker that works for a competitor might be able to steal your technological advances by reviewing your source code.
From a Legal perspective there are three common ways to protect the IP embedded in your code:
Although patents offer the strongest protection, patenting software requires a massive certification process that is slow, expensive, and difficult. For the vast majority of software builders, a patent just isn’t a workable IP protection solution.

In contrast, copyright protection is automatic. You don’t need to mark up your code and copyright law is the basis of most software licenses. However, it comes with its own big issues; it’s limited to copying and distributing content. You can’t copyright algorithms, innovations, or inventions, so if someone else’s code looks nothing like yours or that organization can demonstrate they developed their code in isolation from yours, they’re in the clear. And with managed code, where someone else can generate the same algorithms as yours in multiple languages, copyrighting an application offers little real protection. That leaves trade secrets, which have a lot going for them. There’s no certification, they last forever, and they include concepts, innovations, etc. that give your business financial and competitive advantage. That’s why trade secret protection under the law is increasingly the regulatory strategy of choice for many development organizations.
Sounds perfect, right? Well, trade secret protection has two significant limitations. First, some major jurisdictions – like India, for example – simply don’t recognize the legal concept of a trade secret. The other limitation of trade secret protection is even more fundamental: unlike copyrights and patents, it only covers things that are actually secret. Once something becomes public, it can no longer be protected under trade secret law. More specifically, the definition of trade secret theft requires that possession of a trade secret be achieved through improper means, such as bribery, blackmail, or espionage. Recently enacted trade secret laws, both in the United States (the DTSA) and the European Union, specifically permit reverse-engineering of any legally acquired product. If reverse-engineering your application yields your source code, and therefore, your algorithms, such algorithms may no longer be secrets and no longer covered by trade secret protection.