
Garbage in, garbage out is shorthand for “incorrect or poor quality data will always produce faulty results.”
The “garbage data” vulnerability is especially gnarly in that there is actually no fix – no cure.
The only viable development strategy is one of avoidance.
In short, well-written applications take every opportunity to verify and validate data (and, obviously, to avoid generating garbage data that would ultimately pollute subsequent “downstream” data processing).
Compromised in, compromised out is a modern shorthand for another class of application vulnerability for which there is no fix.
Leaked or otherwise compromised data will always produce compromised results.
Consider the following compromised in, compromised out scenarios:
Compromised data is not “garbage data” in the development sense of the word in that
Yet, compromised data is very much like garbage data in that developers have no viable defense other than avoidance.
As with “garbage data”, well-written applications must take every opportunity to
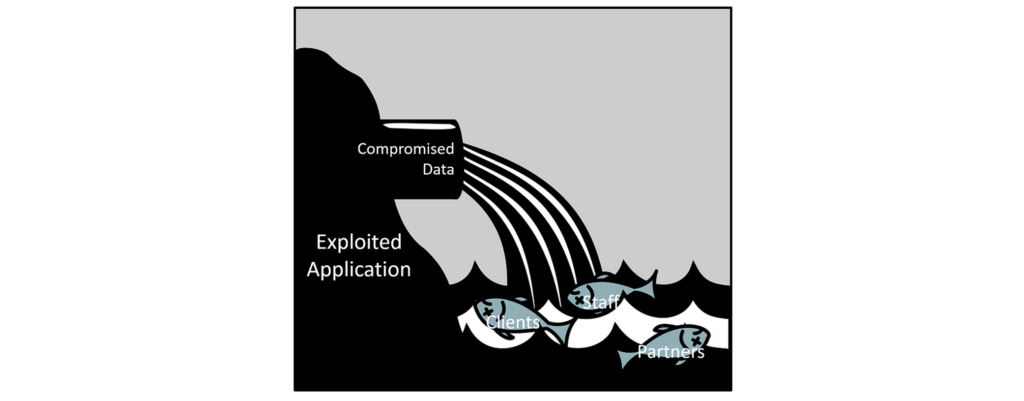
Every application feeding your operation – no matter how small – whether developed by your organization or not – running inside your business or “upstream” inside your suppliers’ and partners’ networks has the potential to pollute (compromise) the systems they feed.
Sound extreme? Consider “Anatomy of the Target data breach: Missed opportunities and lessons learned” where it appears that one of the most damaging data breaches in recent history began with an attack on an air conditioner supplier. Hackers surfed that compromised data stream all the way into Target’s most valuable customer data.
Consider recent regulations like the EU’s GDPR or the recent recommendations from the UK on cybersecurity inside smart cars. Both clearly identify the shared responsibilities of application development organizations across corporate and even international borders to mitigate material privacy, financial, and safety risk – all the way down to small gaps in seemingly minor application functions.
It has never been more important for development organizations to include reasonable, scalable, and reliable controls to avoid, detect, and remediate application exploits – everywhere, not just in obvious, flagship systems.