Today we released Dotfuscator v4.25 that includes, for the first time, anti-debug defense and alert capabilities. Dotfuscator Professional users can now configure Dotfuscator to inject logic to defend against the unauthorized use of a debugger in production. We’ve already previewed this capability in our Java/Android product, DashO, and this latest anti-debug feature sits alongside our other “detective controls” including anti-tamper and shelf-life.
On one hand, a new release of Dotfuscator Professional is not big news – we’re constantly improving our products and this is our fourth Dotfuscator Professional release in the past 12 months – but I think we’ll look back at the inclusion of the anti-debug control as a kind of watershed moment – not in a narrow sense of Dotfuscator’s evolution – but in the evolution of application risk management more broadly.
Why? Here’s (some of) what’s “special” – not “just new.”
Historically, the controls to manage intellectual property theft and software piracy were wholly separate from data integrity and data protection controls. Not true with an effective anti-debug control.Whether a hacker is trying to pirate your app, steal your data, or alter the behavior of a critical piece of infrastructure software as part of a larger crime – a production debugger is always a hacker’s weapon of choice.
As implemented inside Dotfuscator and DashO, the anti-debug control effectively mitigates both risk categories.
Consider how the following exploits that stem directly from debugger hacks cross data, operational, and IP risk boundaries:
| Debugger Hack | Resulting vulnerability and risk |
|---|---|
| Bypassing encryption and other techniques used during data transmission and/or storage exposes otherwise secured data. | Unauthorized data access leads to data loss, loss of revenue, privacy breaches, regulatory non-compliance, and trade secret theft. |
| Insert and modify data within your application | Interrupt application flow circumventing controls and governance and voiding authorization and access controls. |
| Trace logic and the flow of your application | Expose intellectual property for reuse and exploitation |
| View encryption functions, the values of dynamic keys and when and how sensitive information is saved to your file systems and databases | Security and operational breach exposes data and systems beyond any one application. |
Mitigating multiple risk categories brings with it the requirement that event detection and reporting be surfaced inside the dashboard(s) of choice for each stakeholder. Application stakeholders span development, operations, business and audit functions and each brings their own analytics and monitoring requirements and preferences.
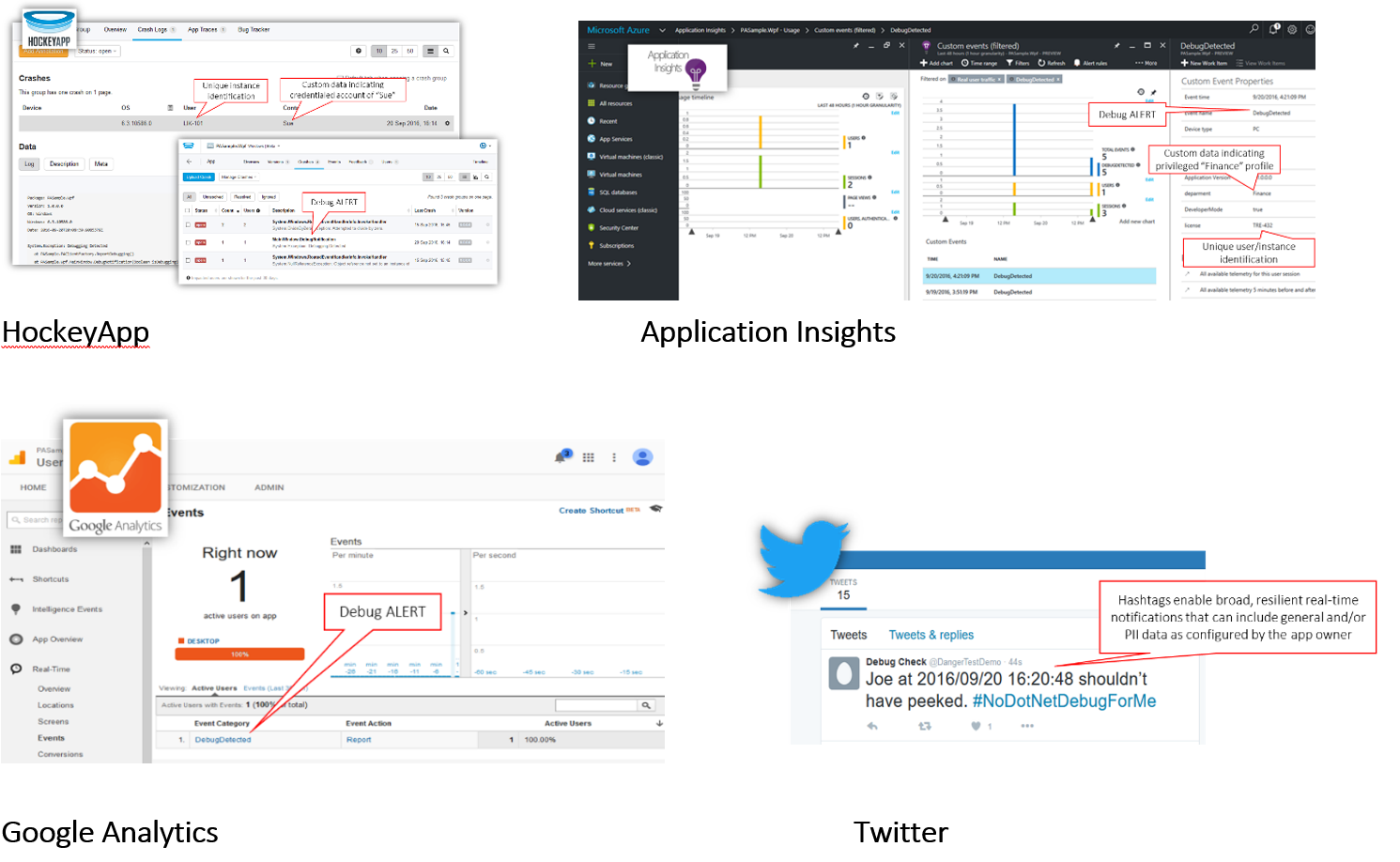
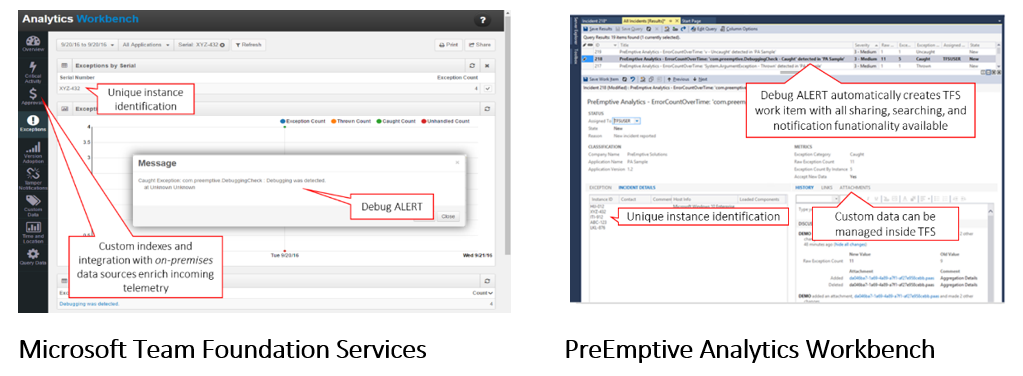
The examples highlighted in this latest Dotfuscator release include multi-tenant cloud services and, if/when required, on-premises options are supported as well. Specifically, the following screenshots show the same telemetry being published inside Microsoft’s HockeyApp and Application Insights, Google Analytics, and even Twitter. For on-premises requirements, we’ve validated event capture inside Microsoft’s TFS and our own PreEmptive Analytics.
On-premises application analytics supporting Dotfuscator’s anti-debug telemetry
In order to be effective, application risk management controls must not
These exacting requirements can only be reliably and consistently met when control implementation, testing, and monitoring is integrated throughout the application lifecycle from design through deployment and into production. For modern development organizations, this translates into integration throughout a “DevOps toolchain.”
Here are concrete examples of what this means for PreEmptive Solutions’ implementation:
Injection post-compile ensures that real-time incident responses are
To learn more (and download a more detailed white paper) and/or evaluate the software described here, visit: Top 5 reasons why Dotfuscator’s new anti-debugging and anti-tamper technology is changing the way developers manage risk.