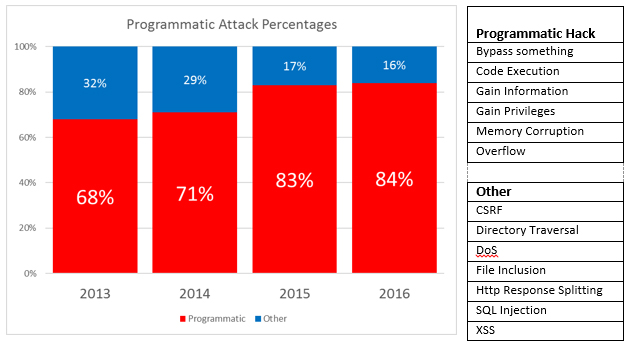
According to NIST’s National Vulnerability Database, six vulnerability categories have grown from 68% to over 84% of the total number of reported vulnerabilities in just the past four years.
What these categories have in common are the tools hackers rely upon to probe, discover, and exploit these increasingly mainstream vulnerabilities. Specifically, hackers begin with application debuggers and reverse engineering tools to pick apart and modify applications. These “programmatic hacks” have led to many of today’s most devastating application and data exploits.

Sources: NIST National Vulnerability Database, Common Vulnerabilities and Exposures (CVE)
Anti-debugger controls can, when combined with code obfuscation (reverse engineering prevention), tamper defense, and other runtime checks, materially reduce application and data risk by impeding (if not outright preventing) the research typically required to identify and exploit application vulnerabilities.
In each of the programmatic CVE categories listed above, a hacker likely began their attack by using some flavor of debugger to explore and manipulate a running instance of an application to bypass security, execute unauthorized code, elevate privileges, etc.
Effective anti-debugger controls mitigate these risks while minimizing potential development, quality, compliance, and/or performance side effects.
PreEmptive Solutions Dotfuscator for .NET and DashO for Java and Android have been developed and continuously improved over the past 15 years to meet these requirements – on desktop, mobile, server, and cloud.
| Platforms (selected) | Real-time defense | Alerts & reporting | Injection (no coding required) | Continuous deployment | |
|---|---|---|---|---|---|
| Dotfuscator | .NET, UWP, Xamarin, etc. | Yes | Yes | Yes | Yes – Visual Studio, VSTS |
| DashO | Java, Android | Yes | Yes | Yes | Yes |
For organizations developing applications worth protecting, visit Harden your .NET Applications with Dotfuscator’s Anti-Debug Protections and PreEmptive Solutions’ Application “Bricking” Gives App Security a Nuclear Option