
The Visual Studio Installer project remains a popular way to deploy .NET applications. It is simple to configure and maintain, and it produces an MSI or EXE that can easily be distributed via a vendor website, software repository, or any other software distribution system.
The installer project places managed assembly files on the end user’s machine. These files can easily be decompiled and reverse-engineered like other .NET applications. This is a significant problem if your app handles sensitive data, contains trade secrets, or has IP that needs to remain hidden.
The good news is this is easy to remediate. We just have to integrate Dotfuscator into our application’s .csproj or .vbproj project file.
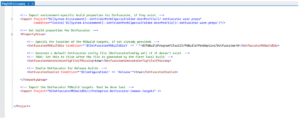
Doing this will trigger Dotfuscator before the packaging steps of a Release build. Dotfuscator places obfuscated assemblies into the release directory, which will automatically be packaged for deployment by the Installer project. No additional steps are required.
This workflow can be implemented for Visual Studio installer projects and works for the most common project deployments: MSIX, ClickOnce, etc. Some projects, however, have non-standard approaches for creating installers. For example, the installer might be decoupled from projects building the assemblies. If this is the case, the Dotfuscator command line interface can be used to automate the handling of protected files.
If you have feedback on this topic or other topics you would like us to discuss in the Support Corner, please contact our Support Team. Your feedback is incredibly valuable to us and helps to shapes the conversations in our Support Corner so we can create a community of shared knowledge and mutual growth. We look forward to hearing from you!