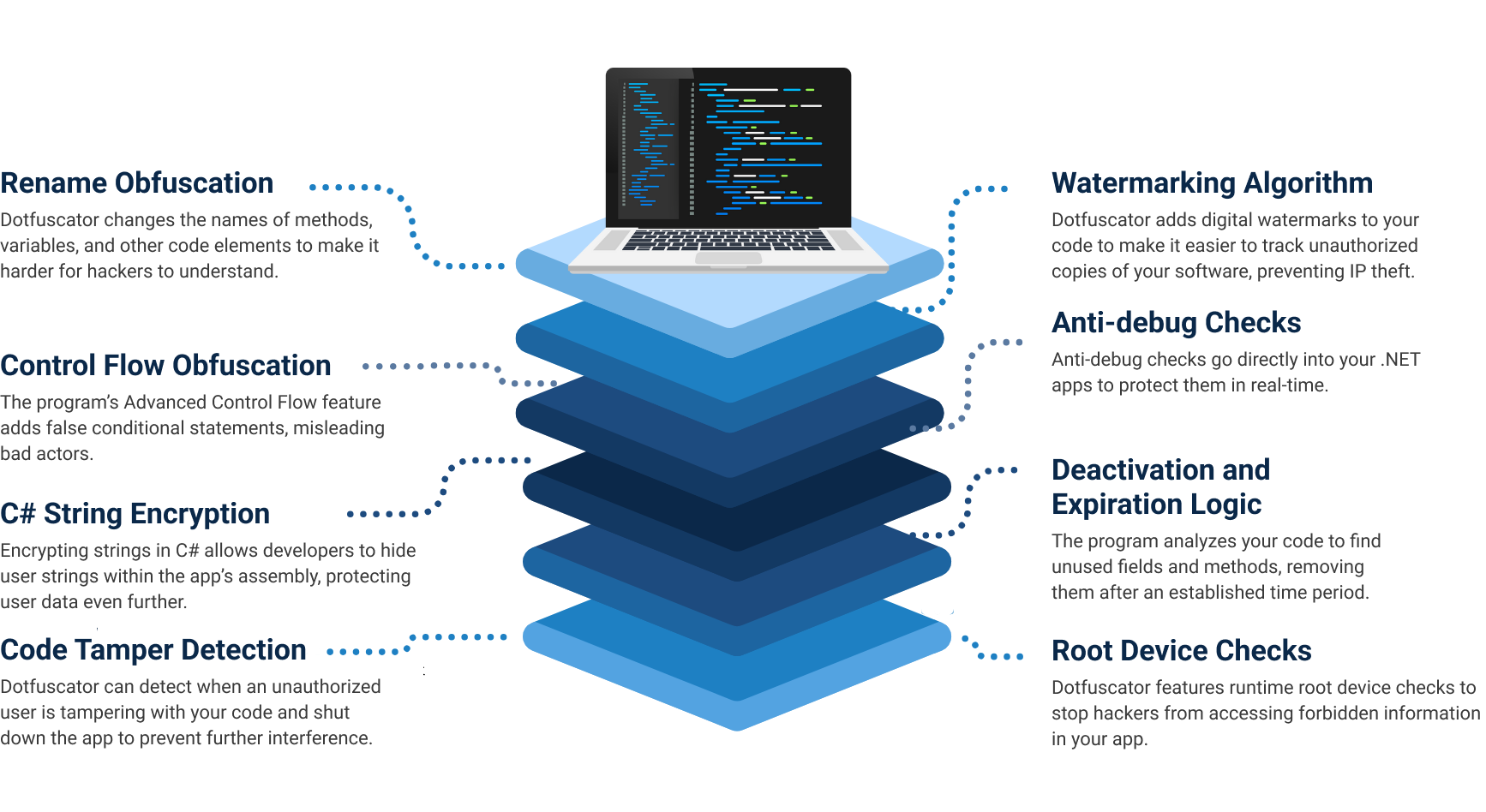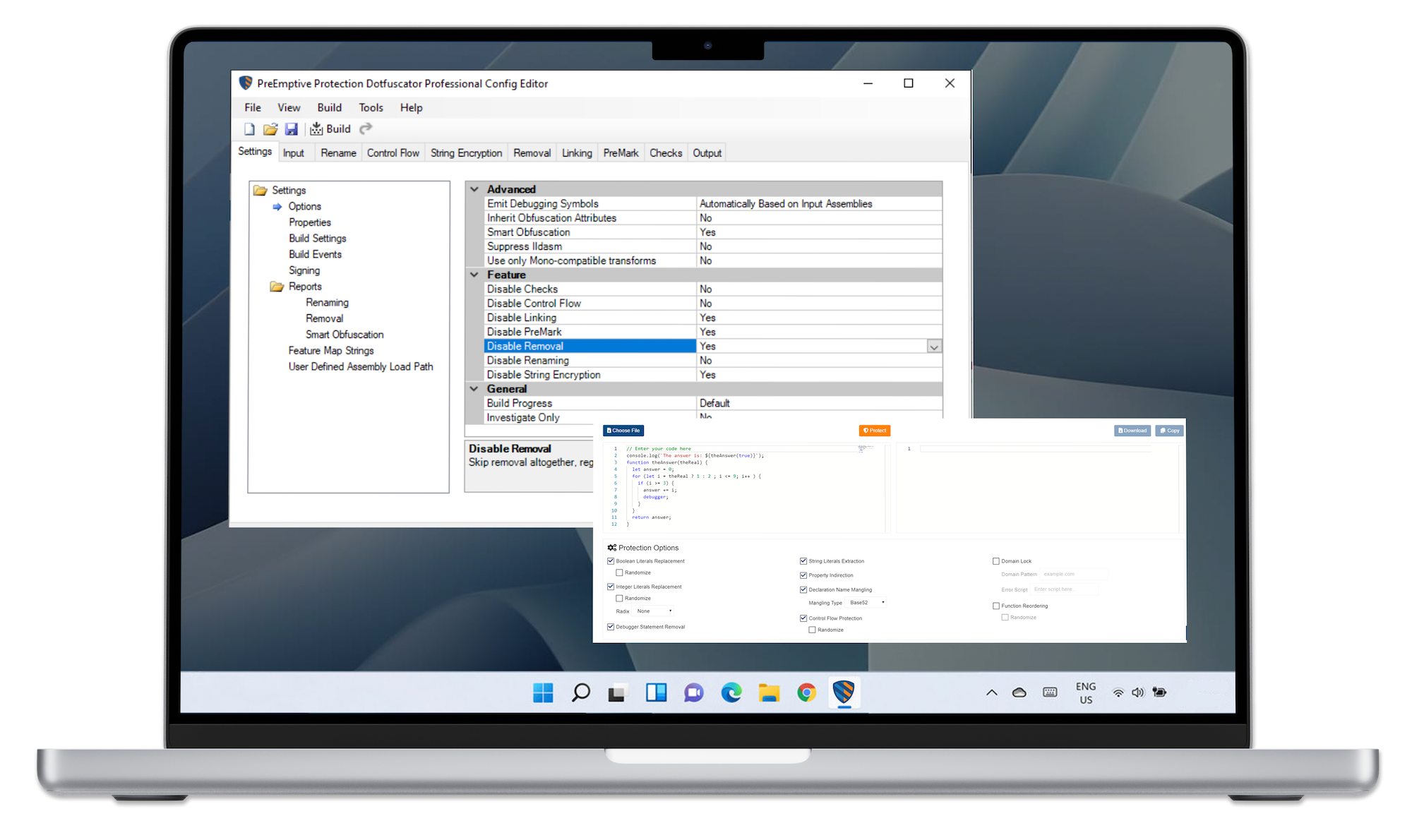



Dotfuscator uses a layered, multi-tiered security approach to protecting MAUI applications. It uses code obfuscation, root detection, app shielding, and tamper-proofing measures to make your applications harder for criminals to exploit.
Dotfuscator goes a step beyond standard rename obfuscation tactics to make your mobile app a less enticing target for hackers. It allows developers to add protection measures directly to the source code with runtime checks, pre-defined response behaviors based on custom logic, and advanced data obfuscation techniques. Some of its encryption features include: