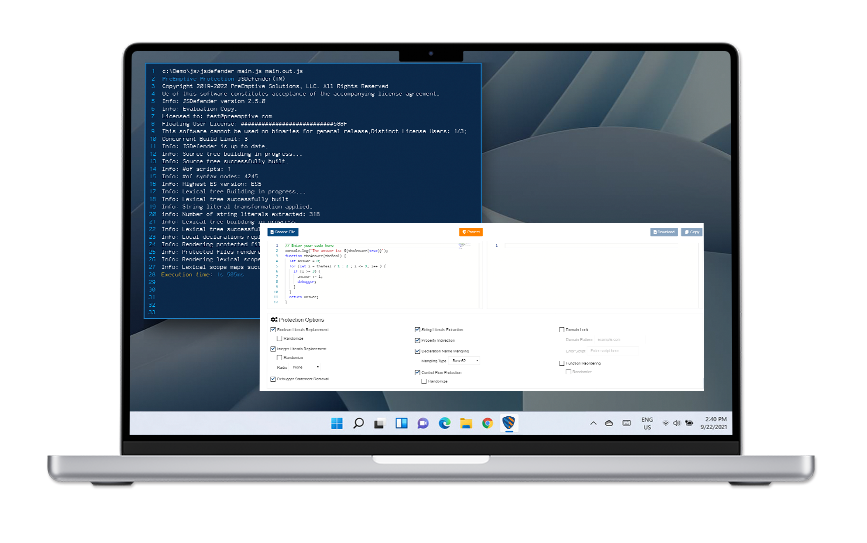



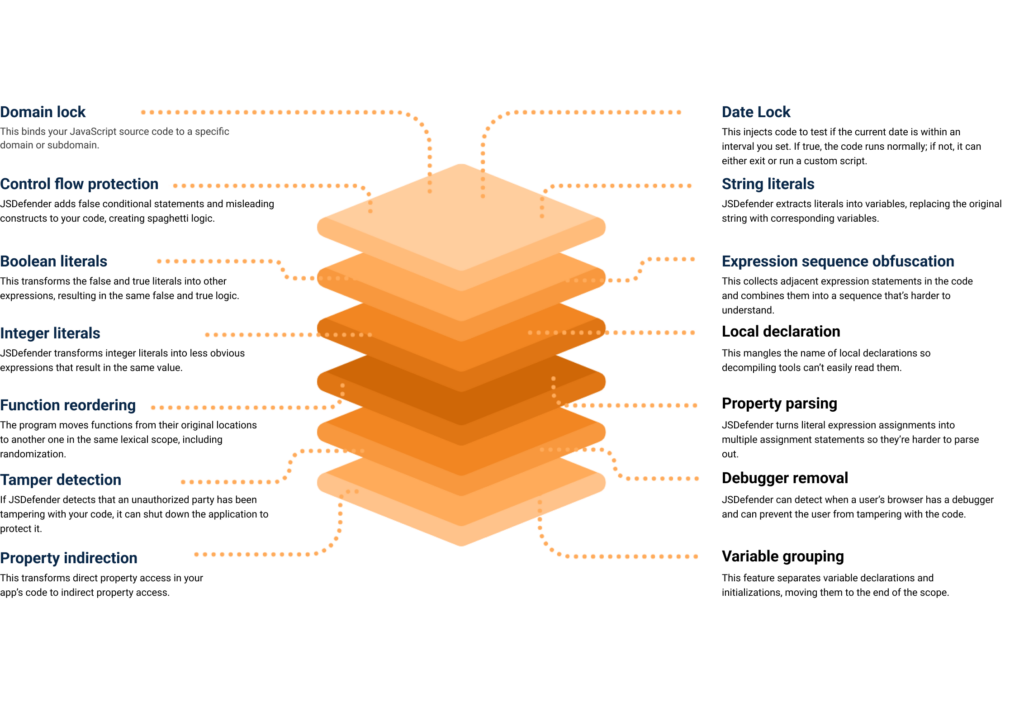
With as many options as the tool has for obfuscating your JavaScript code, JSDefender has hundreds of possible combinations you can use to protect your work. All you have to do is open a command line and start up JSDefender.
From there, JSDefender helps you to scramble and obfuscate the most vulnerable parts of your code, preventing bad actors from being able to tamper with it.
Try our free online obfuscation tool to get a taste of how the program can work for yourself!
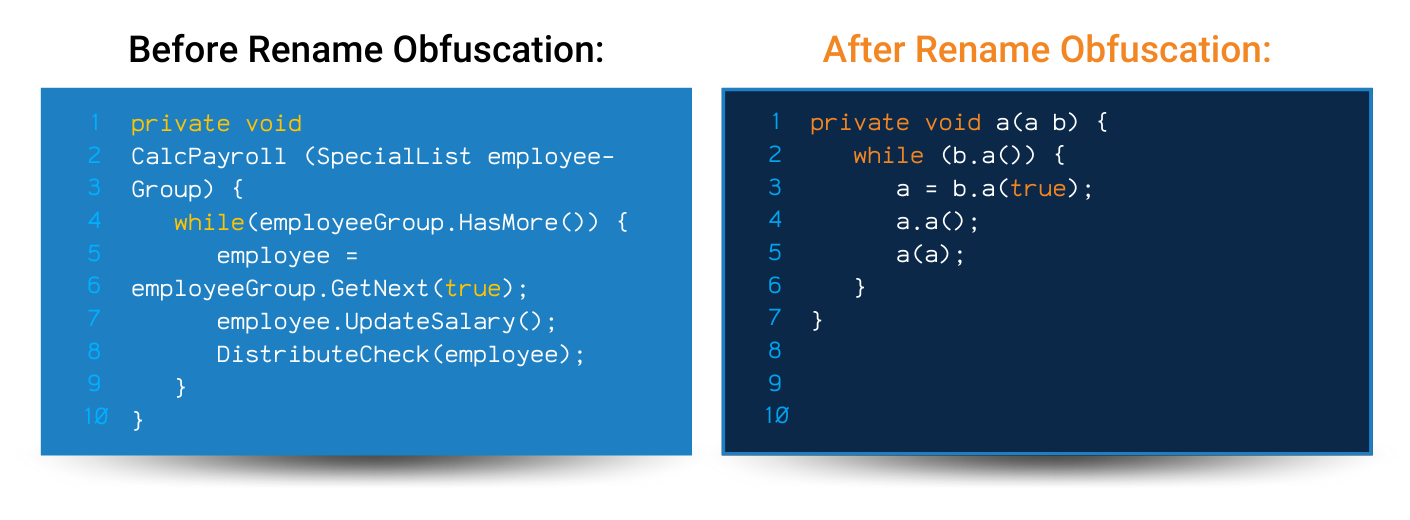

Get started today with a free trial to see how the program gives you watertight security features!
Using JS obfuscation tools allows you to take preventative measures that protect your app and its users from cybercrime, including data breaches, intellectual property theft, piracy, and other threats.
Programs created with JavaScript are particularly at risk of falling victim to reverse engineering. Hackers can use decompilers to easily break into your app and expose the source code. Obfuscating JavaScript code allows you to protect your source code from hackers, making it one of the most practical solutions for having a hardened JavaScript application.
PreEmptive offers a whole suite of application security tools for every type of device and environment your application may need. Some of our other mobile app security options include:
Together, this suite of app hardening tools reduces your attack surface area across Apple products, Android, Java-based applications, and more.
For DevSecOps teams using JSDefender, PreEmptive offers product support from our expert support engineers. They are intimately familiar with JSDefender and its use cases. Should you run into issues that our user guides don’t cover, they’ll be happy to help you solve your problem.
Our support engineers:
No matter which issues you may be experiencing with JSDefender—big or small—our team of experts will help you to make sure you have everything you need when using your JavaScript obfuscation tool.