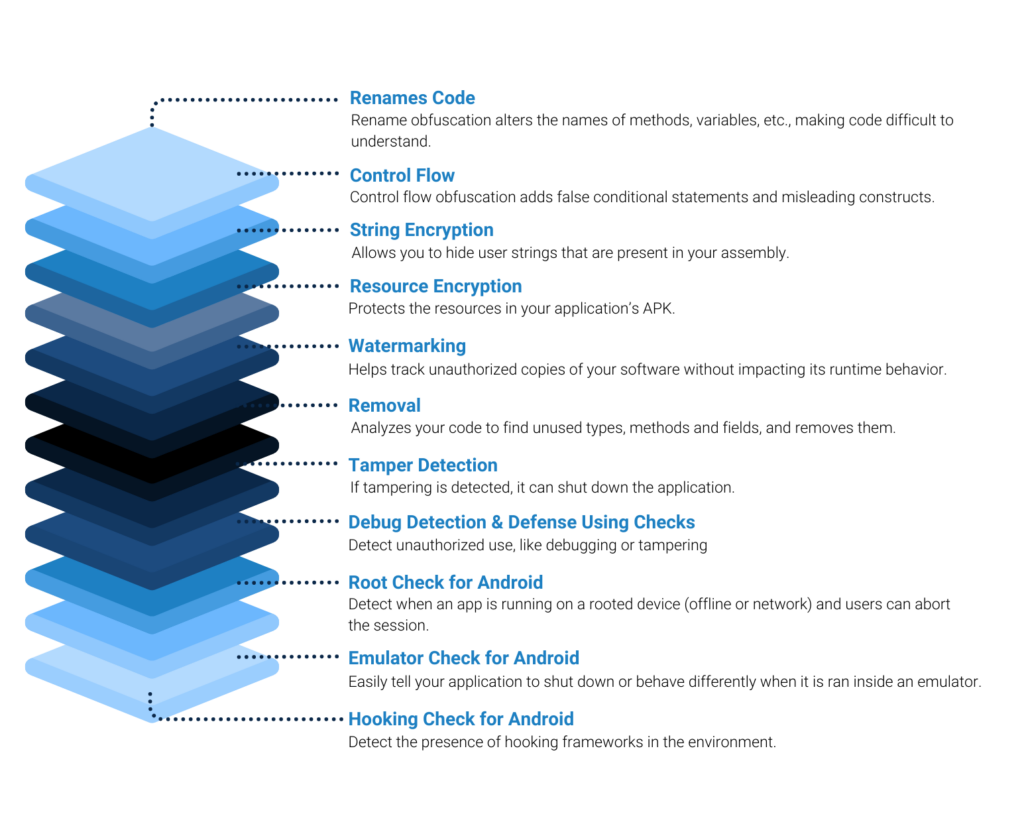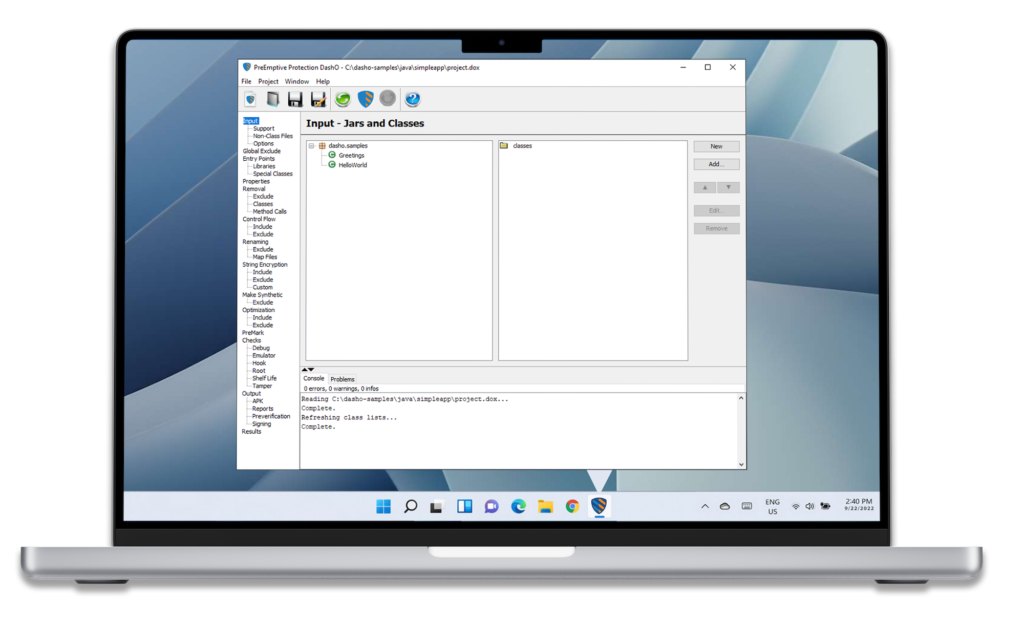

IP Theft: Proprietary business logic can be viewed and/or stolen.
Piracy: License checking mechanisms can be removed.
Credential Bypass: Security and authentication checks may be circumvented.
Fraud: Tampering with in-app payments or collection of login credentials.
Sensitive Information Theft: Debugging or monitoring apps to collect financial, regulated or personally identifiable information.
Code Vulnerability Discovery: Reverse engineering mobile apps can readily expose potential vulnerabilities to attack.
Cloning and Tampering: Apps may be modified with malware and placed on the public app marketplace.
Executing on a Rooted Device: Apps running on a root device may have their integrity compromised.